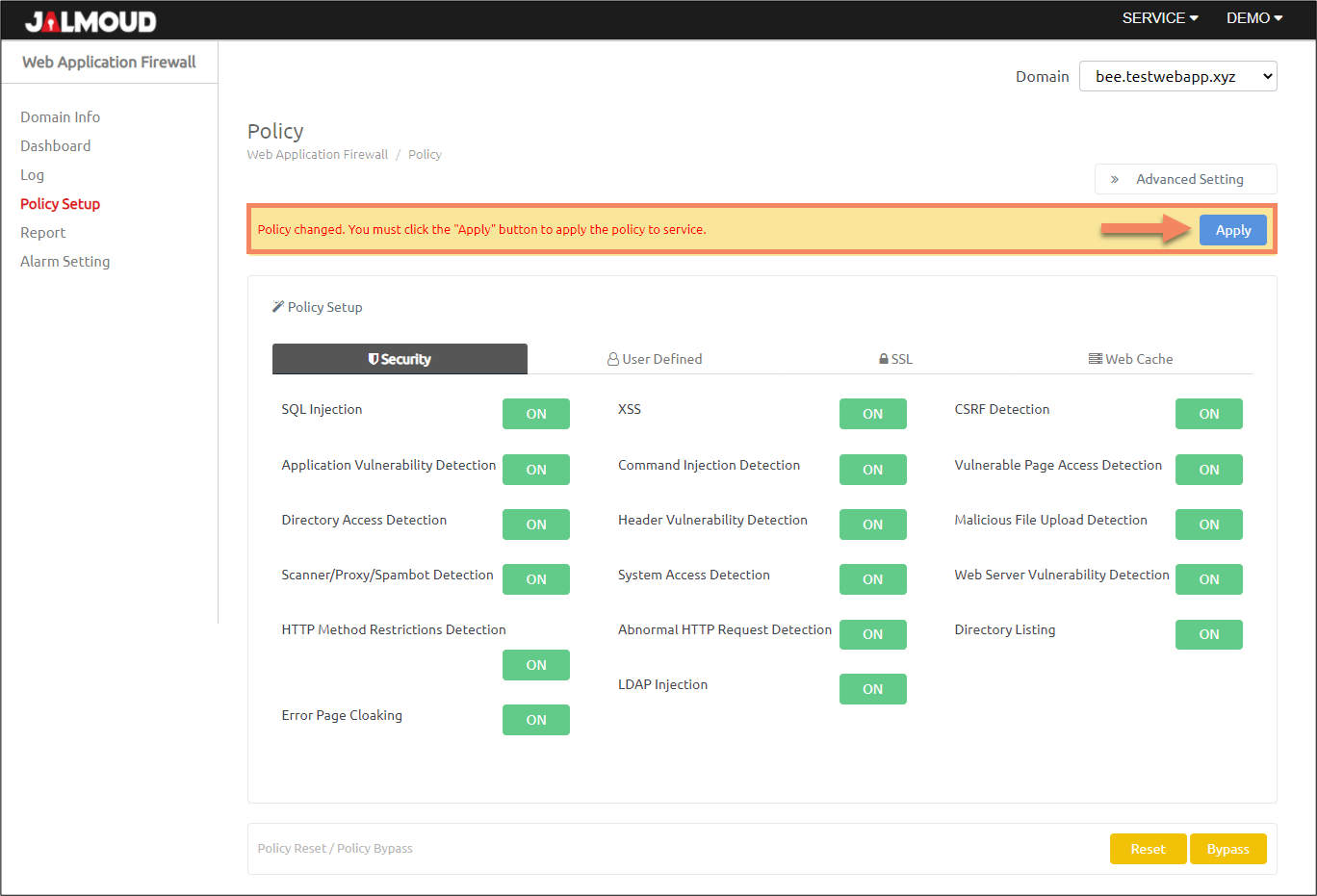
Jalmoud Cloud WAF is a multi-domain and multi-policy solution. This means that you can protect multiple domains or sub domains and for each of them you can define a separate security policy.
You can select the domain first to see its configured security policy at the top of the ‘Policy Setup’ page:
Security Policy #
Below is the security policy that you can customize for each domain.
Click on the ON/OFF button to start the attack policy setup.
- If the policy setup is ‘ON’, it will perform detection and perform blocking.
- If the policy setup is ‘OFF’, it will not detect with the selected policy
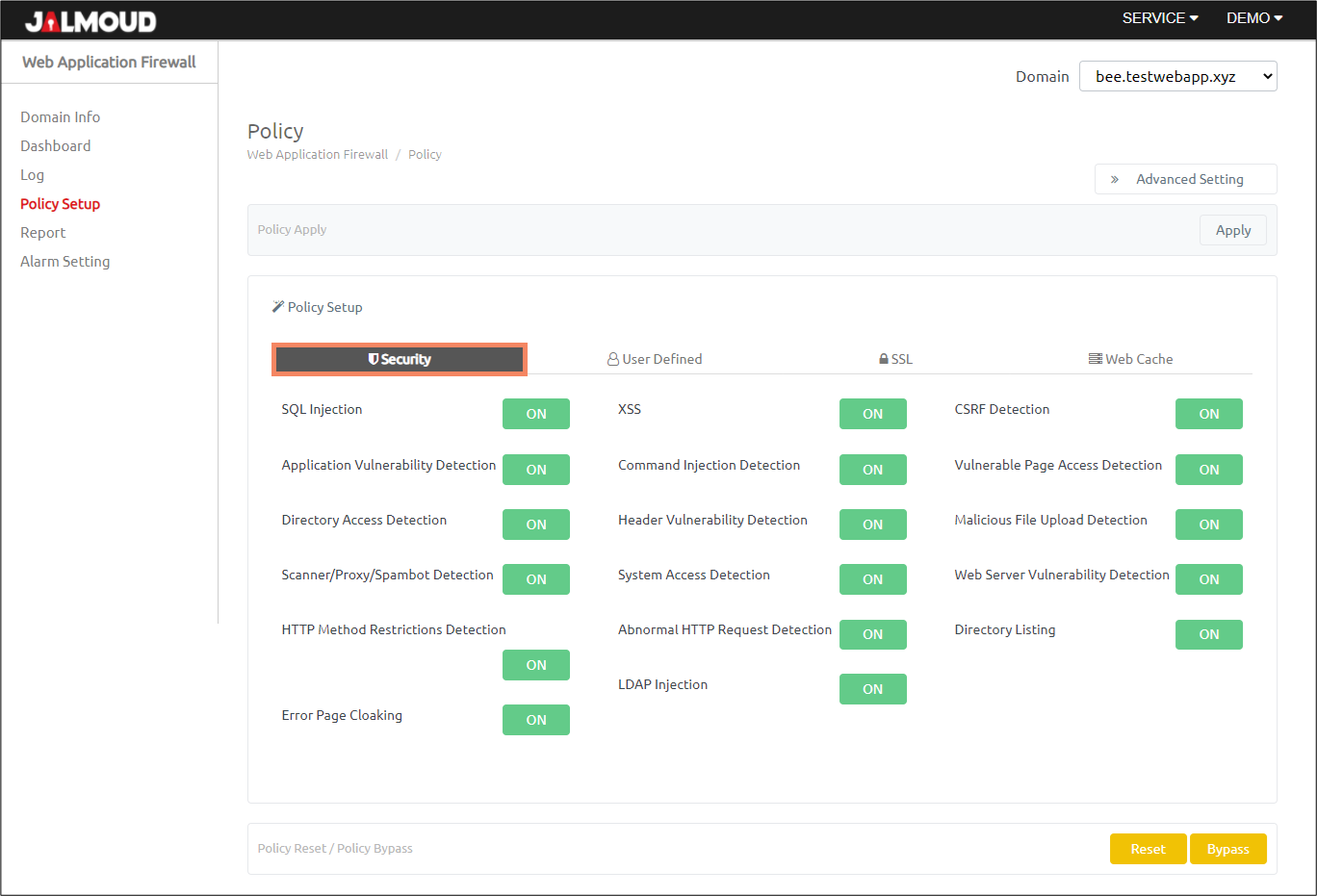
Description of Attack policy #
| Policy | Description |
|---|---|
| SQL Injection | A vulnerability that could allow an attacker to view (or manipulate) information from the DB by inserting SQL statements into the input form and URL fields in a web application that is interfaced with the database(DB). |
| XSS | A vulnerability that could allow an attacker to execute an inappropriate script with the privileges of a visitor who views a Web page by including a malicious script on the page. |
| Scanner/Proxy/Spambot Detection | Crawling, Scraping, Scanner, Web Attack Toolkit, etc., to generate comprehensive attack traffic to detect direct vulnerabilities or collect indirect information to identify vulnerabilities. |
| Web Server Vulnerability Detection | Vulnerability due to inadequate system configuration, such as the presence of installation files and temporary files created during the installation of the application (Apache, etc.), or the windows login window being exposed on the Web. |
| Application Vulnerability Detection | A vulnerability that can be used as an intermediary for homepage tampering and hacking due to various vulnerability information of a public application that is open to the Internet due to financial and time burden in building a web server. |
| CSRF | A vulnerability in which inappropriate scripting is performed with the privileges of the visitor viewing the transmitted dynamic web page when the external input is used to generate the dynamic web page. |
| Malicious File Upload Detection | A vulnerability that the attacker can execute the system internal command or control the system if a script file (asp, jsp, php file, etc.) that can be executed on the server-side can be uploaded and the attacker can execute this file directly through the web. |
| Abnormal HTTP Request Detection | A comprehensive attack mechanism for accessing a web server by manipulating traffic with contradictory standard rules such as multiple spaces, multiple slashes, newline characters, null character insertion, specific header deletion or modulation for security system bypass purposes. |
| Error Page Cloaking | A vulnerability that exposes attack information such as server data information through an error message when a separate error page is not set in the web server. |
| Directory Listing | A vulnerability that could potentially expose sensitive file information by enabling indexing of all directories within the server or directories containing sensitive information. |
| Command Injection Detection | Vulnerability in which unintended system commands are executed when user input values that have not been properly validated are run with some or all of the operating system commands. |
| System Access Detection | A vulnerability that exploits important system information or sensitive information exposed by direct access to important tables or objects of Windows and Unix Web servers in known locations and commercial DBMS servers. |
| Directory Access Detection | A vulnerability that could lead to system information leaks, service failures, etc., because it is possible to construct a path string for an unexpected access restriction area if the characters that can be used for the path manipulation are not filtered for external input values. |
| HTTP Method Restrictions Detection | A vulnerability that allows an attacker to upload malicious files or to delete important files by allowing unnecessary methods (PUT, DELETE, OPTIONS, etc.) when providing Web services. |
| Vulnerable Page Access Detection | A vulnerability that if a file such as an internal document, a backup file, a log file, or a compressed file exists under the web root, the file name can be obtained by inferring, then the service information necessary for hacking can be obtained by directly requesting these file name. Additionally, it is also a vulnerability that could be exploited by various forms of attack, such as an attacker’s SQL injection or brute-force attack, when the administrator’s page is accessible via the Internet. |
| Header Vulnerability Detection | A vulnerability that causes remote command execution or buffer overflow by accessing known vulnerabilities in a web application server or OS system through manipulation of header information such as User-Agent and Range header. |
| LDAP Injection | A vulnerability that tempers with LDAP (application protocol for querying and modifying directory services) query or injects LDAP, thus leaking passwords, personal information, etc. If an LDAP query is performed as part of the user input on the website, change the LDAP syntax to obtain sensitive information within the system. |
User Defined Policy #
This tab allow user to define some additional protection measures.
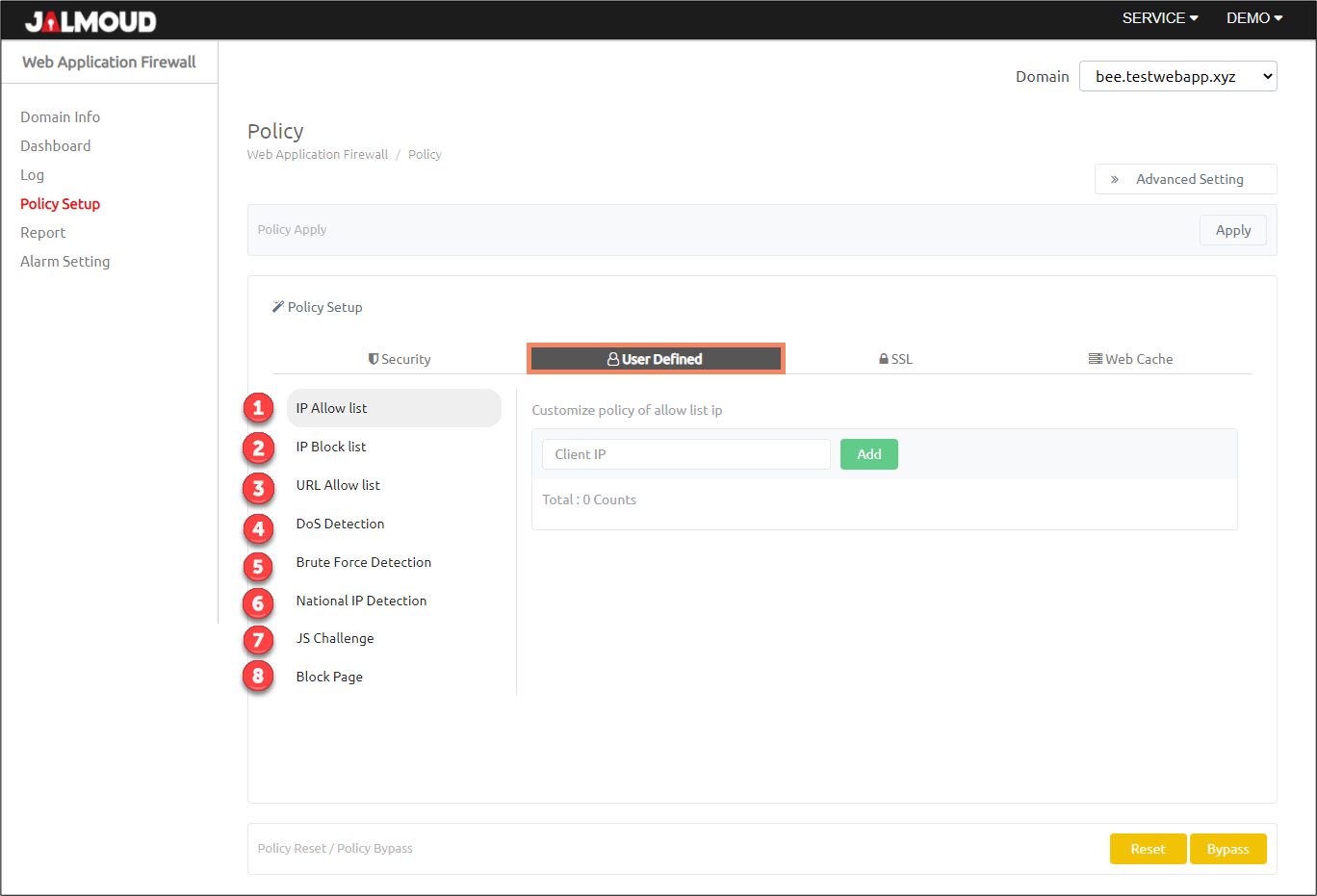
Description of User Defined Policy #
| Item | Description |
|---|---|
| IP Allow list | Bypassing the client IP regardless of other the Web Application Firewall policy after input client IP and apply it. |
| IP Block list | Blocking the client IP regardless of other the Web Application Firewall policy after input client IP and apply it. |
| DoS Detection | Block clients who make much traffic this domain and add these IPs to blocklist. |
| Brute Force Detection | Blocking clients who try to abnormal login attempt to this domain and register this IP to blocklist. |
| URL Allow list | Bypassing the URL regardless of other the Web Application Firewall policy after input URL path and apply it. |
| National IP Detection | National IP Detection blocks the HTTP request which is registered in the untrusted national list before analyzing the data. |
| JS Challenge | Upon receipt of the HTTP request, the WAF responds with a JavaScript challenge script, which can only be interpreted in a web browser. It allows access to the actual website only when interpreting this script, and it defends automated attacks such as bots that cannot be interpreted. |
SSL Policy #
In this tab, you will see information of current installed HTTPS certificate. Moreover, you can change it if you have a situation like expired certificate.
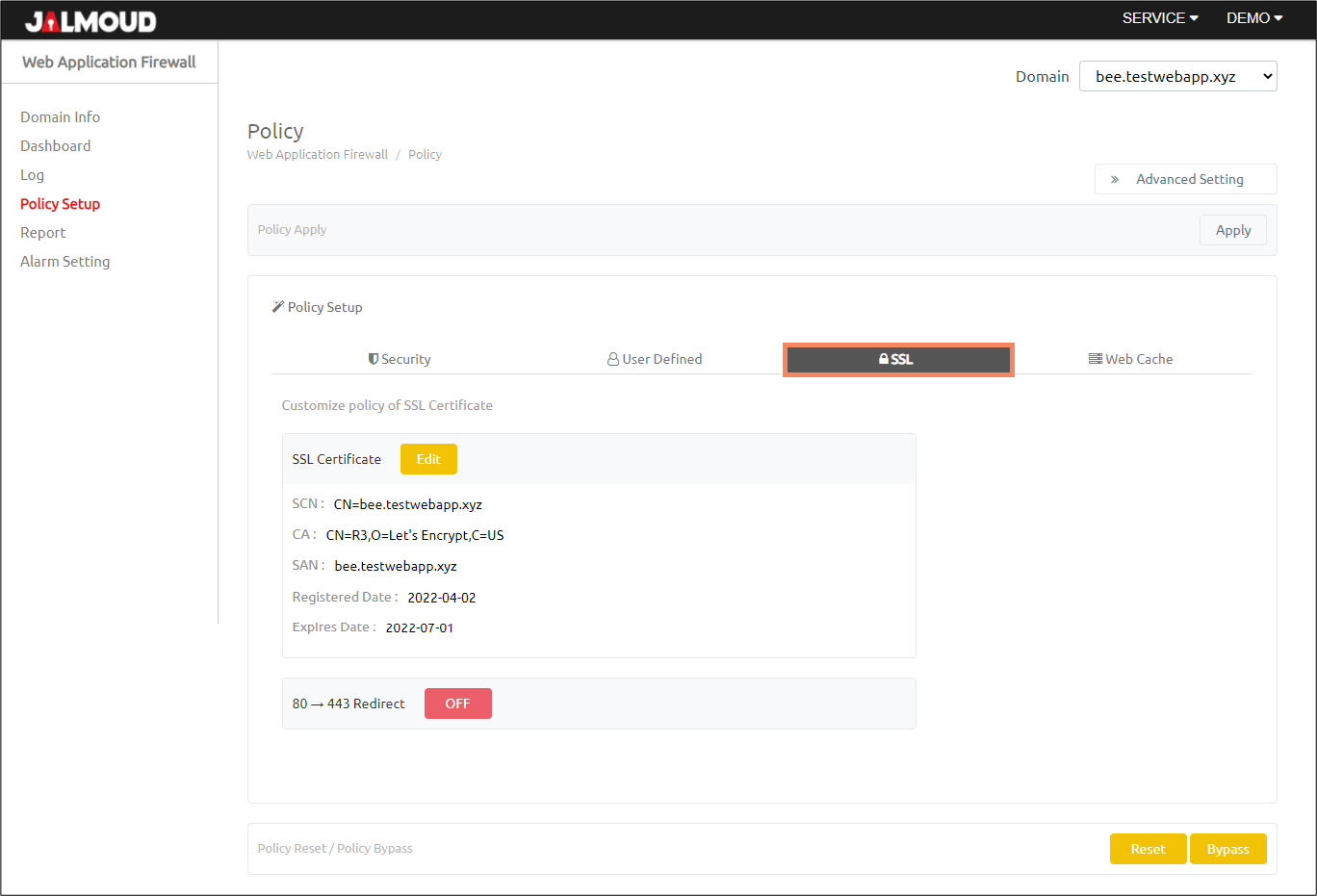
Description of SSL policy #
| Item | Description |
|---|---|
| SSL Certificate | Upload new SSL certificate of your domain for register or change SSL certificate. – Support type: CRT, DER, PEM, PFX, … |
| 80 → 443 Redirect | All traffic of Port 80 (HTTP) redirect to Port 443 (HTTPS). |
Web Cache #
Web cache is a very helpful feature that would save your bandwidth from been consumed so quickly. You can configure a global TTL value (in seconds), and you can exclude URLs from being cached selectively.
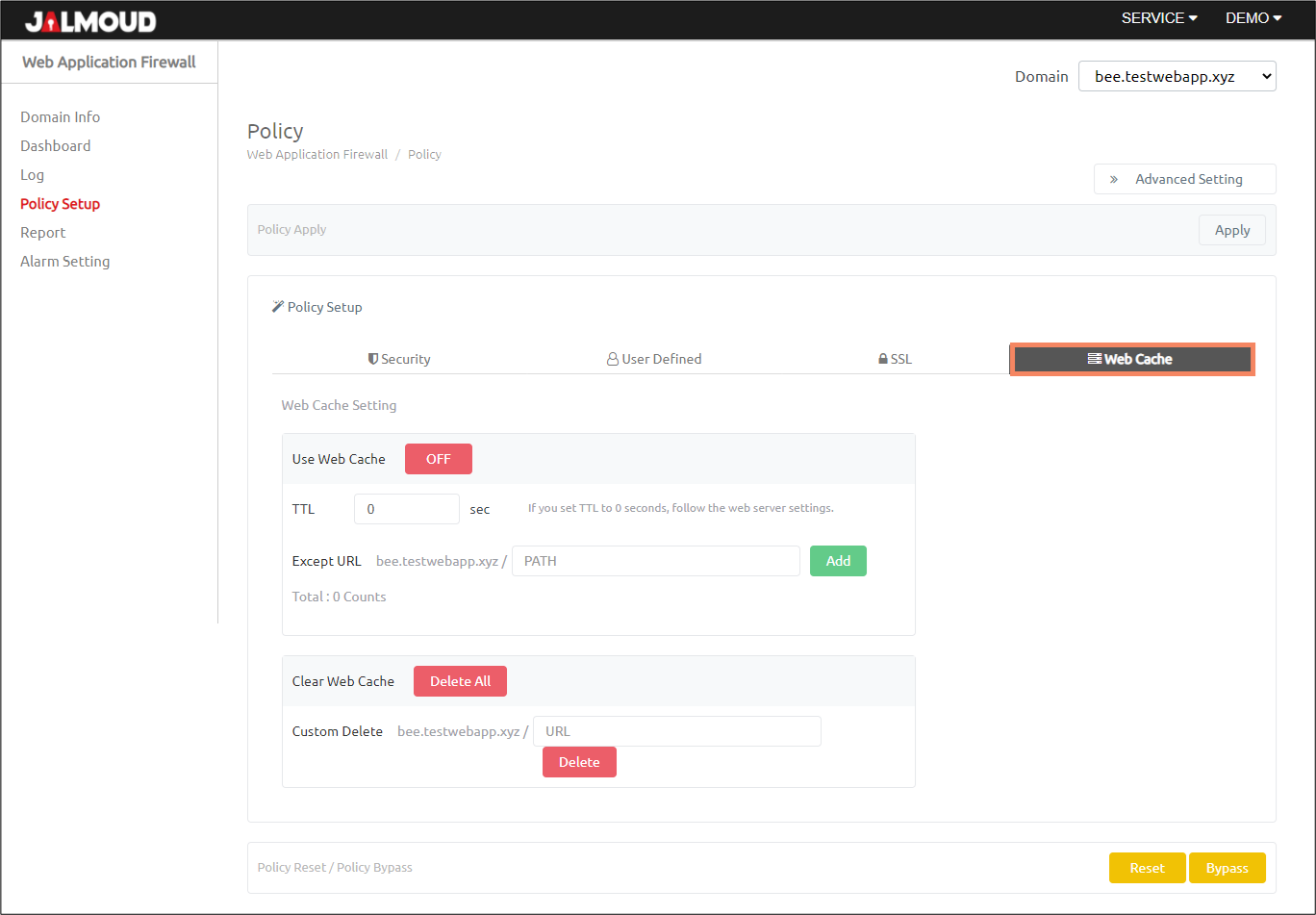
Description of Web Cache Policy #
| Item | Description |
|---|---|
| TTL | Time in seconds for caching web responses to serve later requests. |
| Except URL | Add custom URLs to be excluded from web cache policy. |
| Clear Web Cache | Remove all cached content. |
| Custom Delete | Remove cache related to specific URL. |
Advanced Setting #
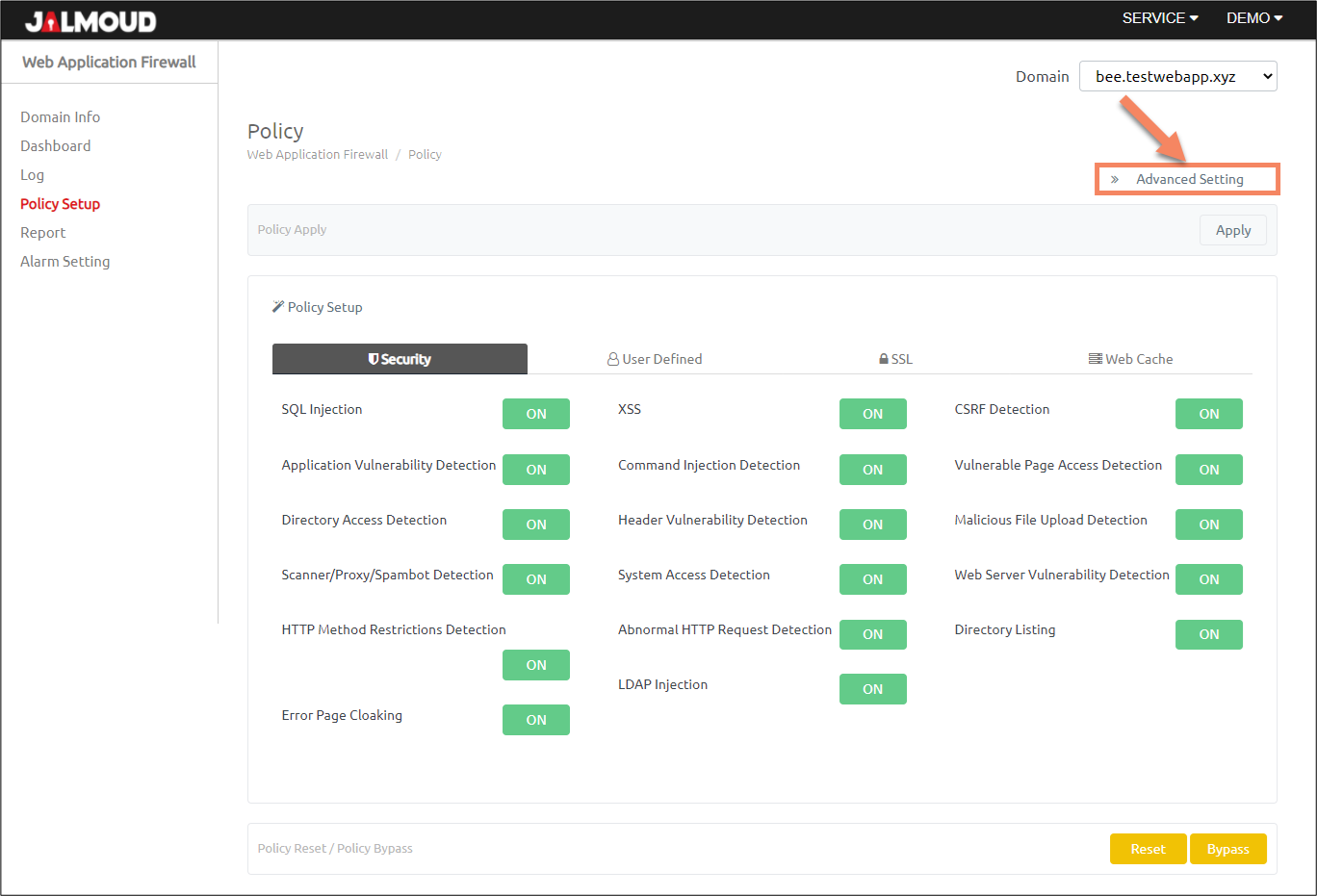
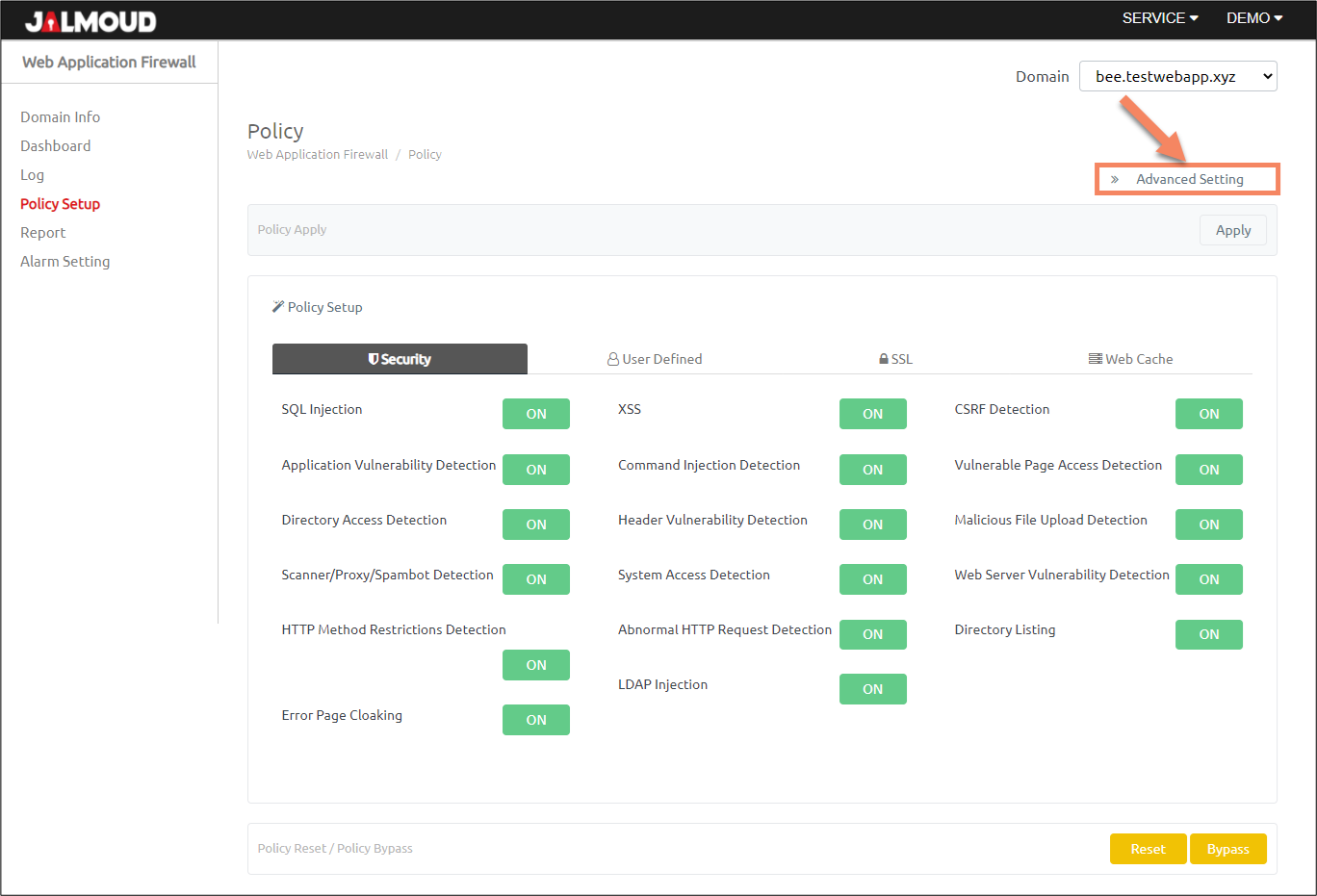
Click on ‘Advanced Setting’ tab.
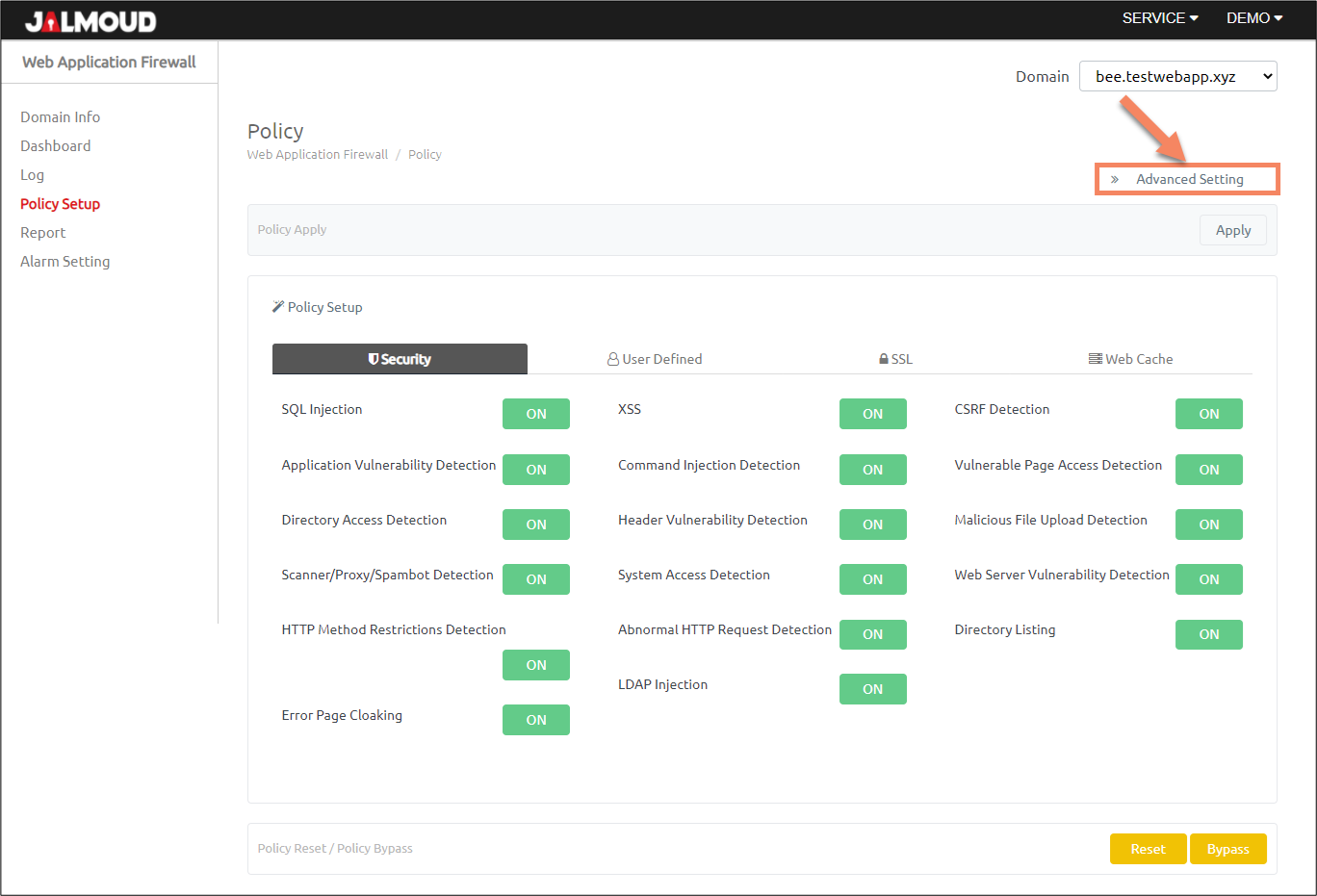
You will see a new pop-up for advanced settings:
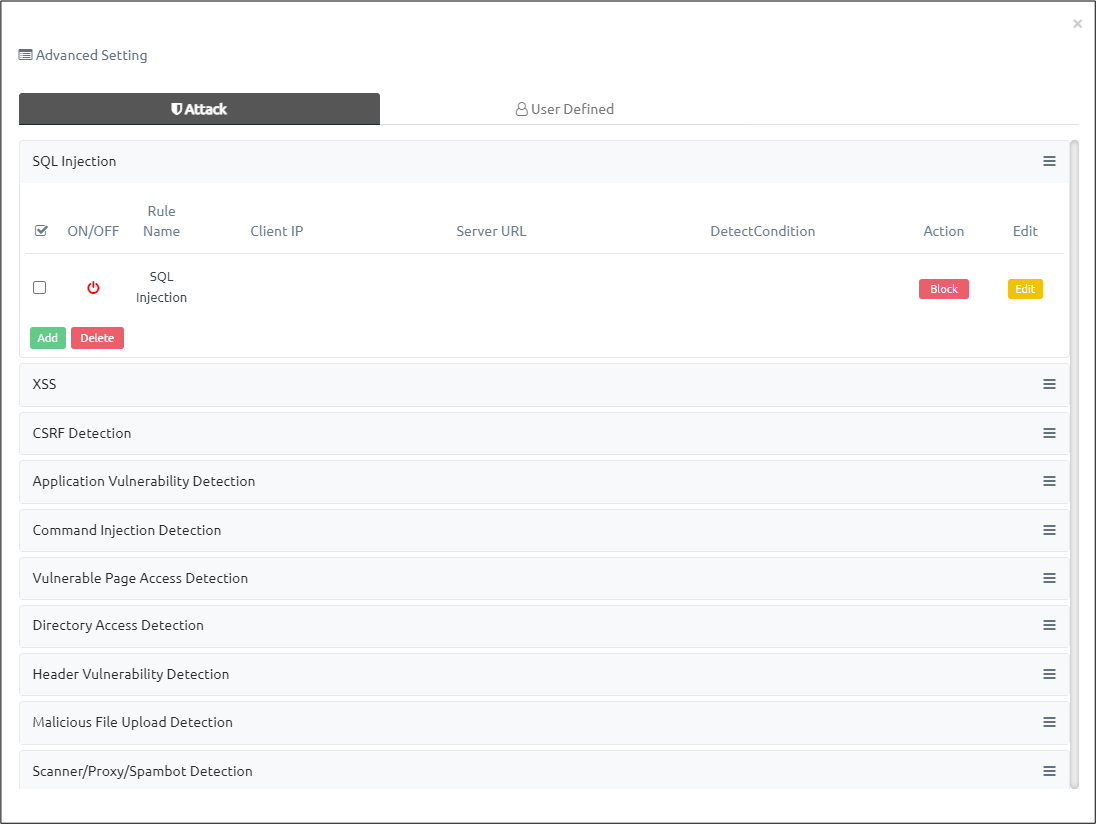
Customize Attack Policy #
In the ‘Attack’ tab, you can whitelist specific URL or IP from attacks activated in ‘Security Policy’.
You can apply customization to all categories of attacks in ‘Attack’ tab:
- Select attack category you want to customize.
- Click on ‘Add’ button.
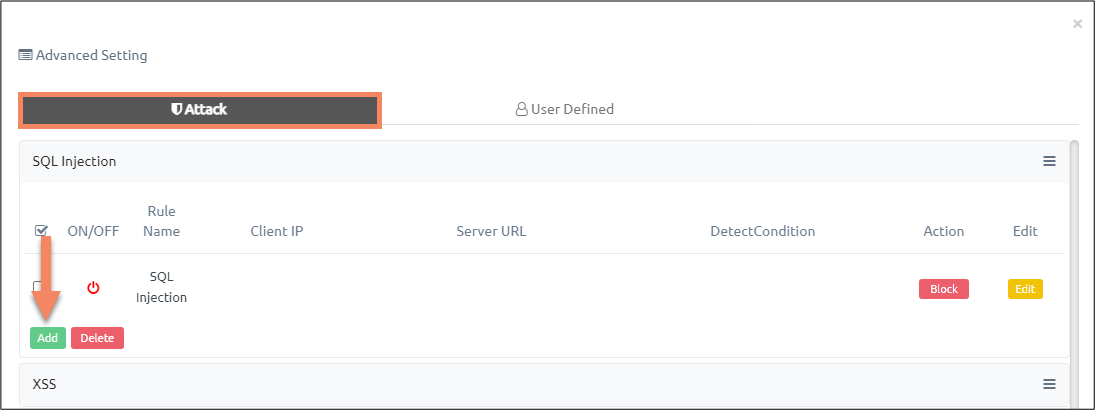
- A pop-up for adjusting or adding security policy appears as below:
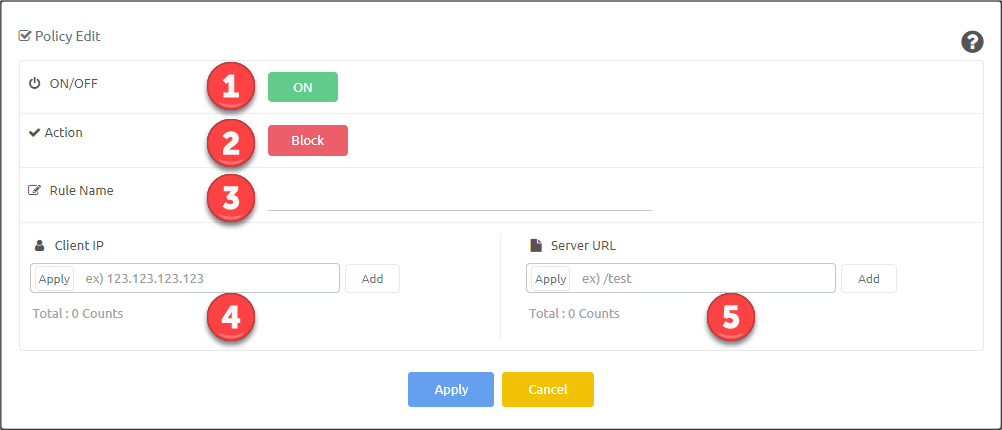
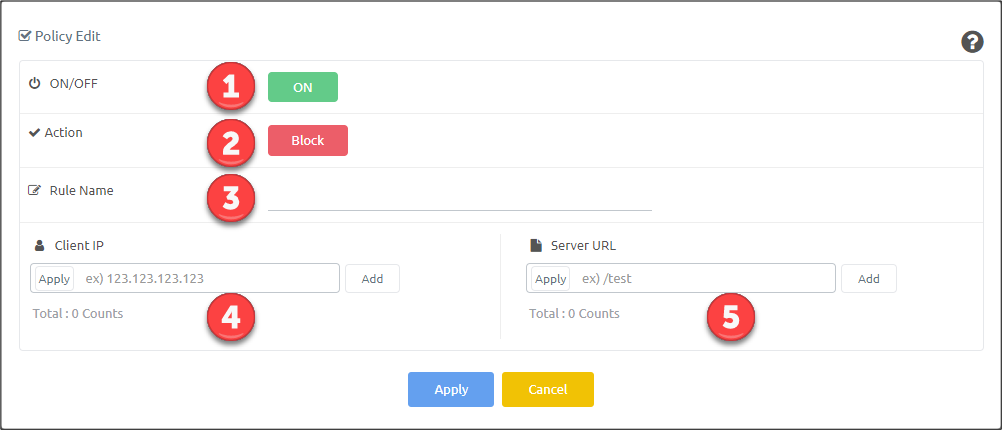
Description of Attack Policy (Advanced) #
| Item | Description |
|---|---|
| ON/OFF | Enable or disable attack policy |
| Action | Set action (Block/Detection) for requests match this policy |
| Rule Name | Name for the rule |
| Client IP | IP of client that will be considered for this rule |
| Server URL | URL of the server that will be considered for this rule |
Customize User Defined Policy #
You have two rules that could be customized:
- URL Access Rule
- Keyword Filter Rule
URL Access Rule #
Using URL access rule, you can blacklist certain IP addresses from accessing specific server page regardless of all other security rules.
First click on ‘Advanced Setting’ button.
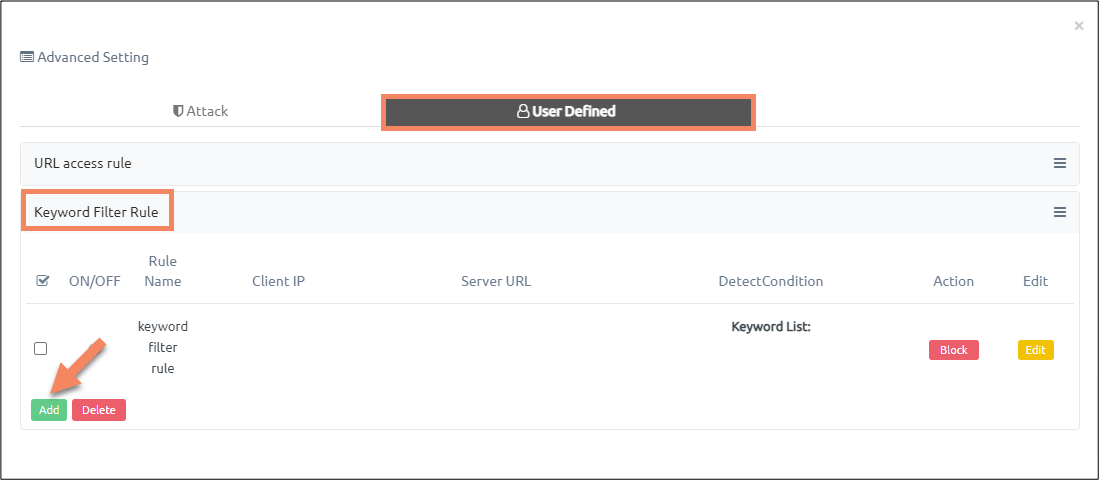
Once you see the pop-up, click on ‘User Defined’, then click ‘Add’ button.
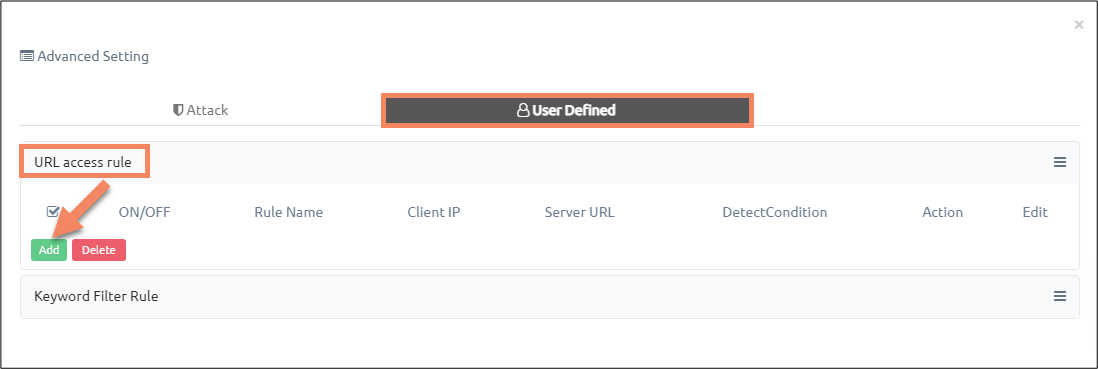
Finally, configure the rule as per your needs.
Keyword Filter Rule #
Using Keyword Filter rule, you can configure blacklisted keywords that should not be observed from the traffic. Keywords allow you to add specific phrases to be detected by the policy as keywords. To configure it, please consider the following steps:
First click on ‘Advanced Setting’ button.
Once you see the pop-up, click on ‘User Defined Policy’, then ‘Keyword Filter Rule’, then click ‘Add’ button.
A new pop-up window will appear to allow you to configure parameters of the rule.
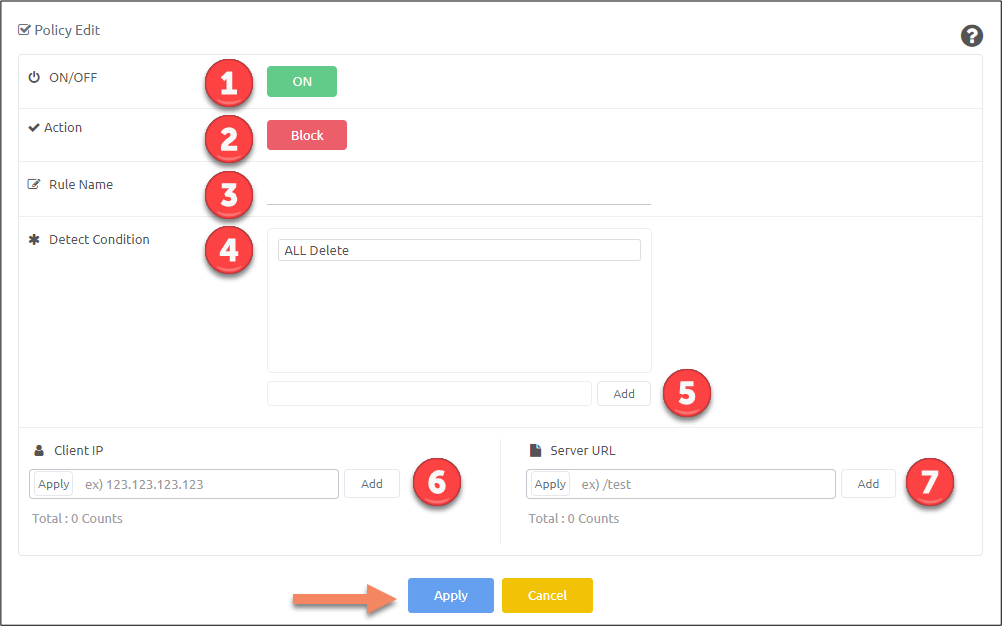
| Item | Description |
|---|---|
| ON/OFF | Enable or disable attack policy |
| Action | Set action (Block/Detection) for requests match this policy |
| Rule Name | Name for the rule |
| Detect Condition | List of all added keywords of the rule |
| Keyword text box | Type keywork and click ‘Add’ button to add it to keywork list |
| Client IP | IP of client that will be considered for this rule |
| Server URL | URL of the server that will be considered for this rule |
Final Step #
Whenever you make changes, make sure you commit the changes. Please note that all policy changes are transparent and doesn’t affect running services.